Start your clients on their cybersecurity compliance journey with Blacksmith InfoSec. Our SaaS application provides each of your customers with bespoke policies, risk management, compliance roadmap, business system user audits, and security awareness training, all with a simple, centralized management platform so you can manage their tenant with white glove service. Set yourself apart from other MSPs today!
Adding new clients to the platform is quick and easy.
Create the policies your clients need based on their unique regulatory landscapes.
Use the Risk Register and Compliance Roadmap to track their progress, facilitate audits, and demonstrate the value of cybersecurity offerings.

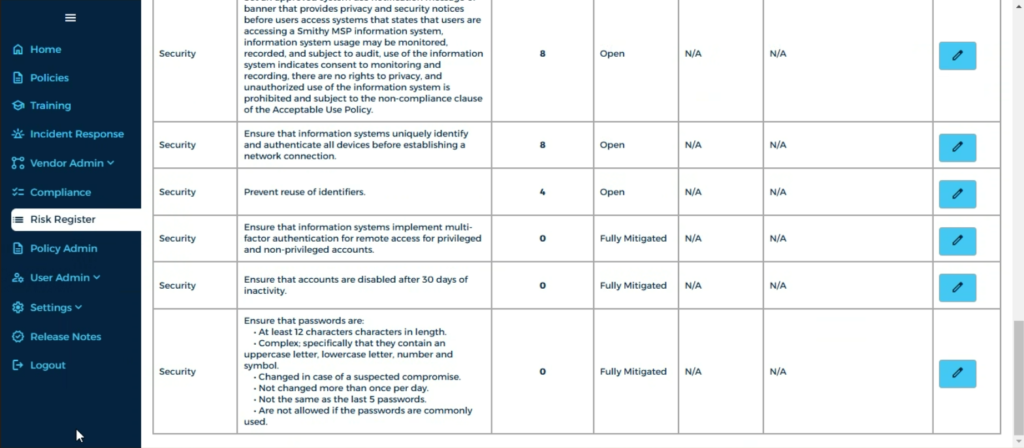
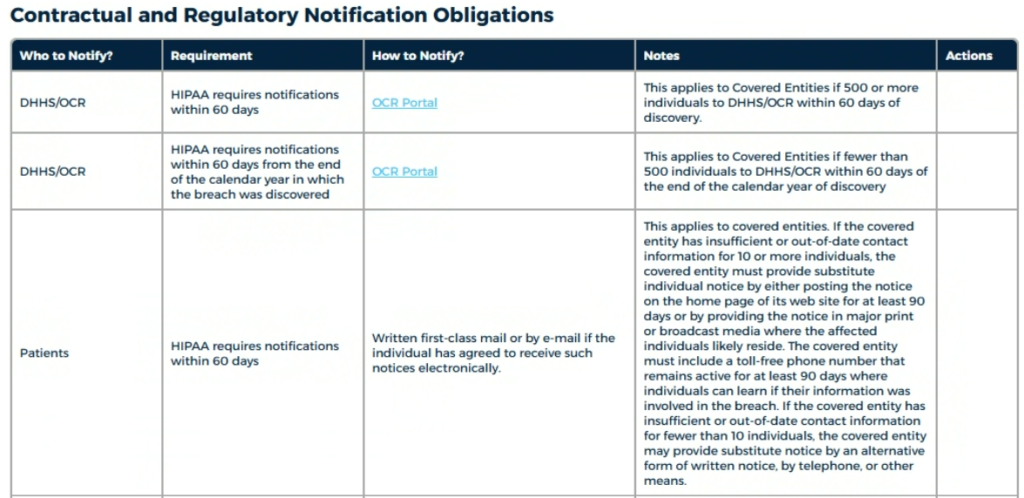
The Blacksmith CaaS platform’s customizable security policies, compliance roadmaps, and risk management tools let you craft tailored solutions for each client’s unique needs.
By streamlining security and compliance processes, you help clients achieve their security goals, tempering confidence and forging long-term partnerships.
